Website Security 2025: Protect Your Site From Hackers
Published by: YAAM Web Solutions Team | Reading Time: 38 minutes
Imagine waking up to find your website defaced, customer data stolen, or your business locked out by ransomware. Unfortunately, this nightmare is becoming reality for thousands of businesses every day. In fact, recent cybersecurity reports reveal that 43% of cyber attacks specifically target small businesses, and the average cost of a data breach has climbed to $4.45 million.
The good news? You don’t need to be a cybersecurity expert to protect your website from hackers. This comprehensive guide will walk you through essential website security 2025 practices that anyone can implement—whether you’re running a small blog, an e-commerce store, or a corporate website.
Table of Contents
Why Website Security Matters More Than Ever in 2025
The digital landscape in 2025 has evolved dramatically, and so have the threats. Cybercriminals are now using sophisticated AI-powered tools and automated bots that scan millions of websites daily, looking for vulnerabilities to exploit. Website security 2025 isn’t just about protecting data—it’s about maintaining customer trust, preserving your brand reputation, and ensuring business continuity.

Here’s what’s at stake:
- Customer Trust: 84% of users abandon websites that display security warnings
- Search Rankings: Google actively penalizes insecure websites in search results
- Financial Impact: Beyond the immediate breach costs, businesses face legal fees, regulatory fines, and lost revenue
- Recovery Time: Without proper security measures, recovery from an attack can take 7-14 days or longer
Whether you’re managing an e-commerce platform or a simple portfolio site, website security best practices should be your top priority. At YAAM Web Solutions, we’ve helped hundreds of businesses implement robust security measures that protect against modern threats while maintaining optimal performance.
Understanding Common Website Vulnerabilities
Before diving into solutions, let’s understand what you’re protecting against. Knowing about common website vulnerabilities helps you implement targeted defenses that actually work.
The Top Security Threats in Website Security 2025
1. SQL Injection Attacks
Attackers manipulate database queries through input fields, potentially accessing or deleting sensitive information. Despite being well-known, SQL injection remains a critical threat, with 25% of web applications still vulnerable to this attack method.
2. Cross-Site Scripting (XSS)
Malicious scripts are injected into trusted websites, compromising user data and sessions. This vulnerability allows attackers to steal cookies, session tokens, and other sensitive information directly from your users’ browsers.
3. Brute-Force Attacks
Automated tools systematically try thousands of password combinations until they find the right one. Brute-force attack protection is essential because weak passwords remain one of the leading causes of security breaches.
4. DDoS (Distributed Denial of Service) Attacks
Your website gets overwhelmed with fake traffic, making it unavailable to legitimate users. DDoS attack protection mechanisms help ensure your site remains accessible even during attacks.
5. Malware Infections
Malicious software gets installed on your server, often creating backdoors for future attacks. Malware protection for websites involves both prevention and regular scanning to detect infections early.
6. Phishing and Social Engineering
Attackers trick your team members into revealing login credentials or installing malicious software. This threat highlights why employee training is a crucial component of website security 2025.
7. Zero-Day Exploits
Hackers exploit previously unknown vulnerabilities before developers can patch them. Staying informed and working with security-conscious development teams helps mitigate these risks.
Understanding these threats is the first step in website hacking prevention. Now let’s explore how to protect your website from hackers with practical, implementable solutions.
Essential Website Security Best Practices
Implementing website security best practices doesn’t require a massive budget or advanced technical skills. These foundational steps protect against 85% of common cyber attacks and build immediate user trust.
1. Install SSL Certificate and Enable HTTPS (The Foundation of Website Security 2025)
SSL and HTTPS importance cannot be overstated. An SSL/TLS certificate encrypts all data transferred between your visitors’ browsers and your server, protecting sensitive information like login credentials, payment details, and personal data from interception.
Why This Matters:
- Browsers now flag non-HTTPS sites as “Not Secure,” potentially driving away visitors
- Google prioritizes HTTPS sites in search rankings
- Protects against man-in-the-middle attacks where hackers intercept data
How to Implement:
- Purchase an SSL certificate from your hosting provider or use free options like Let’s Encrypt
- Install the certificate on your server (most hosts offer one-click installation)
- Update your website configuration to redirect all HTTP traffic to HTTPS
- Configure HSTS (HTTP Strict Transport Security) to enforce HTTPS at the browser level
- Monitor SSL expiration dates and renew certificates before they expire
Pro Tip: At YAAM Web Solutions, we include SSL certificate installation and automatic renewal in all our hosting packages, ensuring your site maintains continuous encryption without manual intervention.
2. Implement Strong Authentication Methods
Weak passwords and stolen credentials are responsible for the majority of security breaches. Implementing robust authentication is a critical website security tip that dramatically reduces your attack surface.
Two-Factor Authentication for Admin Panel
Two-factor authentication for admin panel adds an extra security layer by requiring two forms of verification before granting access. Even if an attacker obtains your password, they can’t access your account without the second factor (usually a code sent to your phone or generated by an authentication app).
Implementation Steps:
- Enable 2FA for all admin and privileged accounts
- Use authenticator apps like Google Authenticator, Authy, or Microsoft Authenticator
- Store backup codes in a secure location
- Require 2FA for hosting control panels, FTP access, and database management tools
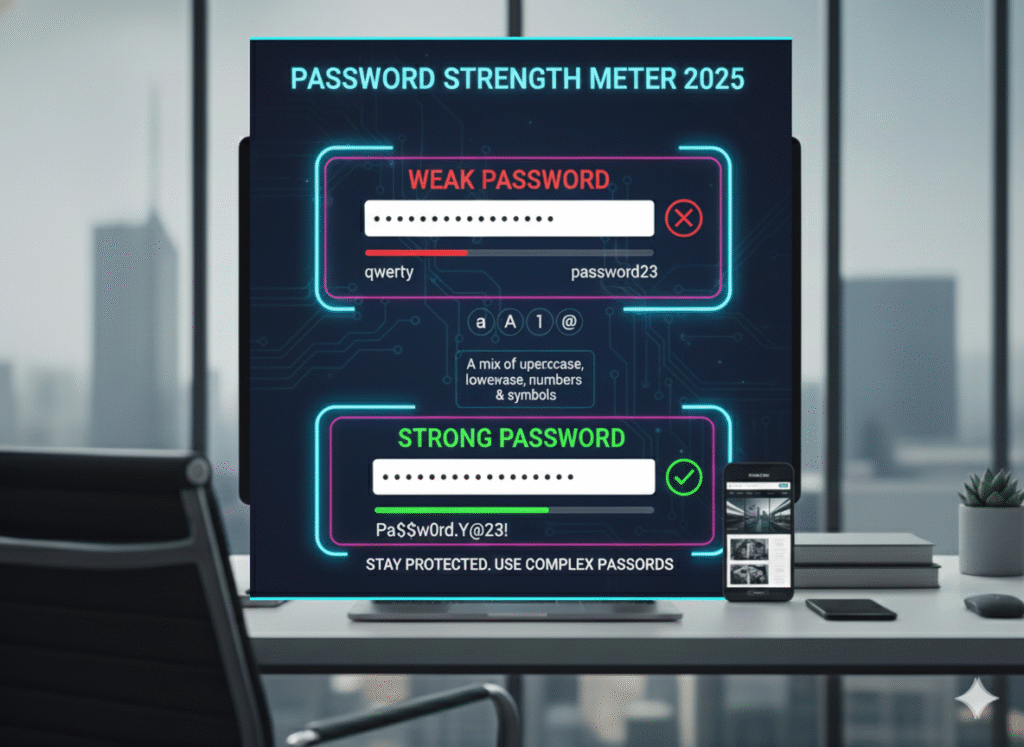
Password Best Practices:
- Enforce minimum password length of 12 characters
- Require a mix of uppercase, lowercase, numbers, and special characters
- Implement password expiration policies (change every 90 days)
- Use password managers to generate and store complex passwords
- Never reuse passwords across different platforms
Website Security 2025 Insight: Multi-factor authentication reduces breach risk by 99.9%, making it one of the most effective security measures available.
3. Keep Everything Updated (Critical for Website Hacking Prevention)
Outdated software is the number one cause of website hacks. Attackers actively scan for known vulnerabilities in popular platforms, themes, and plugins. This website security tip is simple but often overlooked.
What Needs Regular Updates:
- CMS core files (WordPress, Joomla, Drupal, etc.)
- All plugins and extensions
- Themes and templates
- Server software (PHP, MySQL, etc.)
- SSL certificates
Best Practices:
- Enable automatic updates for minor security patches
- Test major updates on a staging environment first
- Remove unused plugins and themes completely
- Subscribe to security bulletins from your CMS provider
- Maintain an update schedule and stick to it
Real-World Example: The infamous Revolution Slider WordPress plugin vulnerability from 2014 is still actively exploited today because many websites never updated. Don’t become another statistic—make updates part of your routine website security 2025 strategy.
4. Deploy a Web Application Firewall (Essential Website Firewall Benefits)
A Web Application Firewall (WAF) acts as a protective shield between your website and the internet, filtering malicious traffic before it reaches your application. Understanding website firewall benefits helps you appreciate why this tool is essential for comprehensive protection.
How WAFs Protect Your Website:
- Block SQL injection attempts automatically
- Prevent cross-site scripting (XSS) attacks
- Mitigate DDoS attacks by filtering suspicious traffic patterns
- Stop brute-force login attempts
- Block traffic from known malicious IP addresses
Popular WAF Solutions:
- Cloudflare (offers free and premium tiers)
- Sucuri (specialized in website security)
- AWS WAF (for Amazon-hosted sites)
- Wordfence (WordPress-specific)
Implementation Considerations:
- Cloud-based WAFs are easier to set up and maintain
- Some hosting providers include WAF protection in their packages
- Configure custom rules based on your specific needs
- Monitor WAF logs regularly to identify attack patterns
The website firewall benefits extend beyond just blocking attacks—they also improve performance through content caching and optimization.
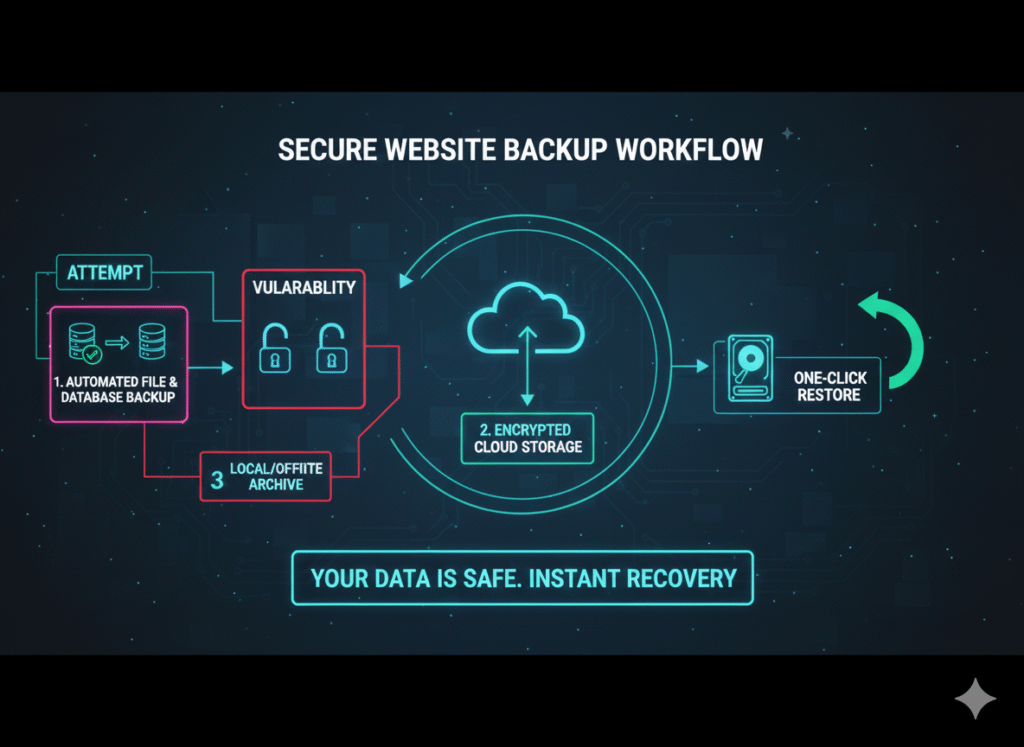
5. Regular Website Backups (Your Safety Net)
Regular website backups are your last line of defense. Even with all security measures in place, breaches can still occur. Comprehensive backups ensure you can restore your site quickly, minimizing downtime and data loss.
Backup Best Practices:
- Frequency: Automate daily backups for active websites
- Storage: Keep copies in multiple locations (local, cloud, and offsite)
- Scope: Include both files and databases
- Encryption: Encrypt backups before uploading to cloud storage
- Testing: Verify backup integrity by testing restoration quarterly
What to Backup:
- All website files
- Database contents
- Configuration files
- Email accounts and data
- SSL certificates and keys
Recovery Benefits:
- Reduces recovery time from weeks to 2-4 hours
- Protects against ransomware attacks
- Provides peace of mind
- Enables quick rollback if updates cause issues
Website Security 2025 Reality Check: According to recent studies, websites with proper backup systems recover 93% faster from security incidents compared to those without.
Need a comprehensive backup solution? YAAM Web Solutions offers automated backup services with encrypted cloud storage and one-click restoration.
How to Prevent Website Attacks: Advanced Strategies
Beyond basic security measures, these advanced strategies significantly strengthen your website security 2025 posture and help you protect website from hackers more effectively.
Input Validation and Sanitization
Always treat user input as potentially malicious. Proper validation prevents SQL injection and XSS attacks:
- Use parameterized queries or prepared statements for database operations
- Sanitize all user inputs before processing
- Implement Content Security Policy (CSP) headers
- Validate data types and formats on both client and server sides
Implement Rate Limiting
Rate limiting controls how frequently users can make requests to your server, protecting against:
- Brute-force login attempts
- DDoS attacks
- API abuse
- Form spam
Configuration Tips:
- Limit login attempts to 5 per 15 minutes
- Implement CAPTCHA after failed attempts
- Use IP-based rate limiting for API endpoints
- Monitor and adjust thresholds based on legitimate traffic patterns
Least Privilege Access
Grant users only the minimum permissions necessary for their roles:
- Create separate accounts for different team members
- Avoid using admin accounts for daily tasks
- Regularly audit user permissions
- Remove accounts for former employees immediately
- Implement role-based access control (RBAC)
Security Headers Configuration
Properly configured HTTP security headers add an extra layer of protection:
X-Frame-Options: DENY
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Content-Security-Policy: default-src 'self'
Strict-Transport-Security: max-age=31536000; includeSubDomains
These headers help prevent clickjacking, MIME type sniffing, and other common attacks.
WordPress Security: Special Considerations for 2025
WordPress powers over 40% of all websites, making it a prime target for attackers. Secure WordPress website 2025 requires platform-specific security measures beyond general best practices.
Essential Security Plugins for WordPress
Security plugins for WordPress provide comprehensive protection with minimal configuration. Top recommendations include:
1. Wordfence Security
- Real-time firewall protection
- Malware scanning
- Login security features
- Two-factor authentication
- Traffic monitoring
2. Solid Security (formerly iThemes Security)
- Brute-force protection
- Database backups
- File change detection
- Security hardening recommendations
3. Sucuri Security
- Security activity auditing
- File integrity monitoring
- Remote malware scanning
- Security hardening
WordPress-Specific Security Measures
Change Default Settings:
- Modify the default admin username (never use “admin”)
- Change the database prefix from “wp_” to something unique
- Disable file editing in the WordPress dashboard
- Limit login attempts
Secure wp-config.php:
define('DISALLOW_FILE_EDIT', true);
define('FORCE_SSL_ADMIN', true);
Protect Important Files:
- Add .htaccess rules to protect sensitive files
- Disable directory browsing
- Block access to wp-config.php and .htaccess
Regular Security Audits:
- Review user accounts monthly
- Check for suspicious files in uploads directory
- Monitor failed login attempts
- Audit installed plugins for unused or outdated ones
XML-RPC Protection:
Disable XML-RPC if you’re not using it, as it’s commonly exploited for brute-force attacks:
<Files xmlrpc.php>
Order Deny,Allow
Deny from all
</Files>
Choosing a Secure Hosting Provider
Your hosting provider forms the foundation of your website security 2025 strategy. Choosing a secure hosting provider is one of the most critical decisions you’ll make.
What to Look for in a Security-Focused Host
Server-Level Security:
- Regular security patches and updates
- DDoS protection
- Intrusion detection systems
- Network-level firewalls
- Isolated hosting environments
Backup Services:
- Automated daily backups
- Multiple backup retention periods
- Easy restoration options
- Offsite backup storage
SSL/TLS Support:
- Free SSL certificates included
- Automatic certificate renewal
- Support for modern encryption protocols
Monitoring and Support:
- 24/7 security monitoring
- Malware scanning
- Expert security support team
- Incident response procedures
Compliance and Certifications:
- PCI DSS compliance (for e-commerce)
- GDPR compliance features
- ISO 27001 certification
- SOC 2 certification
Red Flags to Avoid
- Shared hosting with unlimited sites on one server
- No mention of security measures
- Outdated server software
- Poor customer reviews regarding security incidents
- Lack of backup options
At YAAM Web Solutions, our hosting infrastructure includes enterprise-grade security features typically reserved for large corporations, making them accessible to businesses of all sizes. Explore our secure hosting solutions designed specifically for website security 2025.
How to Monitor Website Security Continuously
Implementing security measures is just the beginning. Knowing how to monitor website security ensures you detect and respond to threats before they cause significant damage.
Essential Monitoring Tools and Practices
1. Security Scanning Tools
- Sucuri SiteCheck (free online scanner)
- Qualys SSL Labs (SSL configuration testing)
- OWASP ZAP (comprehensive security testing)
- Acunetix (vulnerability scanning)
2. Uptime Monitoring
- UptimeRobot (free uptime monitoring)
- Pingdom (advanced monitoring with alerts)
- StatusCake (website monitoring)
3. File Integrity Monitoring
- Set up alerts for unauthorized file changes
- Monitor critical files like wp-config.php, .htaccess
- Use plugin-based solutions or server-level tools
4. Log Analysis
- Review access logs weekly
- Monitor for suspicious login attempts
- Check for unusual traffic patterns
- Analyze 404 errors (often indicate probing attacks)
Setting Up Alerts
Configure notifications for:
- Failed login attempts exceeding threshold
- Unauthorized file changes
- Website downtime
- SSL certificate expiration
- Unusual traffic spikes
- Malware detection
Pro Tip: Centralize security logs using tools like ELK stack (Elasticsearch, Logstash, Kibana) or Grafana Loki for comprehensive visibility across your infrastructure.
Regular Security Audits
Schedule comprehensive security audits:
- Monthly: Review user accounts and permissions
- Quarterly: Full vulnerability scan and penetration testing
- Annually: Complete security assessment by external auditors
Many breaches go undetected for months because organizations lack proper monitoring. Don’t let this happen to you—make monitoring a core component of your website security 2025 strategy.
Website Security Checklist: Quick Reference Guide
Use this secure website checklist to ensure you’ve implemented all essential security measures. Print this out and check off each item as you complete it.
Immediate Actions (Do Today)
- [ ] Install SSL certificate and force HTTPS
- [ ] Enable two-factor authentication for admin accounts
- [ ] Update all CMS core files, plugins, and themes
- [ ] Set up automated daily backups
- [ ] Change default admin username and password
- [ ] Install a security plugin or WAF
- [ ] Remove unused plugins, themes, and accounts
- [ ] Disable file editing in CMS dashboard
Weekly Security Tasks
- [ ] Review failed login attempts
- [ ] Check for available updates
- [ ] Verify backup completion
- [ ] Monitor website uptime reports
- [ ] Review security plugin logs
Monthly Security Tasks
- [ ] Audit user accounts and permissions
- [ ] Review and update passwords
- [ ] Check SSL certificate expiration date
- [ ] Analyze website traffic patterns
- [ ] Test backup restoration process
- [ ] Review security headers configuration
Quarterly Security Tasks
- [ ] Conduct full security scan
- [ ] Perform penetration testing
- [ ] Review and update security policies
- [ ] Train team members on security awareness
- [ ] Evaluate new security tools and services
- [ ] Update incident response plan
Annual Security Tasks
- [ ] Complete comprehensive security audit
- [ ] Review hosting provider security measures
- [ ] Update disaster recovery plan
- [ ] Evaluate compliance requirements
- [ ] Review and renew security certifications
Following this secure website checklist consistently significantly reduces your vulnerability to attacks and helps establish a culture of security awareness within your organization.
AI and Machine Learning in Website Security 2025
Artificial intelligence is revolutionizing how we approach website security 2025. Modern security systems now use machine learning algorithms to detect and respond to threats faster than any human could, making AI-powered security essential for staying ahead of increasingly sophisticated attacks.
How AI Enhances Website Security
1. Intelligent Threat Detection
AI-powered security systems analyze millions of data points in real-time, identifying unusual patterns that indicate potential attacks. These systems learn from each encounter, becoming more effective at spotting threats over time.
Benefits include:
- Detection of zero-day exploits before they’re widely known
- Identification of subtle attack patterns humans might miss
- Automatic blocking of suspicious traffic in milliseconds
- Reduced false positives compared to traditional rule-based systems
2. Predictive Security Analytics
Machine learning models can predict potential vulnerabilities by analyzing your website’s code, configuration, and traffic patterns. This proactive approach helps you patch security holes before attackers discover them.
3. Automated Incident Response
AI systems can automatically respond to detected threats by:
- Temporarily blocking suspicious IP addresses
- Isolating compromised accounts
- Initiating backup protocols
- Alerting your security team with detailed context
4. Behavioral Analysis for User Authentication
Advanced AI systems track normal user behavior patterns, flagging unusual activities like:
- Login attempts from unfamiliar locations
- Unusual data access patterns
- Suspicious admin panel activities
- Abnormal file uploads or modifications
AI-Powered Security Tools for 2025
Darktrace: Uses self-learning AI to detect and respond to cyber threats across cloud, email, network, and endpoint environments.
Cloudflare Bot Management: Employs machine learning to distinguish between legitimate users and malicious bots.
Security.ai: Provides automated penetration testing using AI to continuously scan for vulnerabilities.
Vectra AI: Offers AI-driven threat detection and response specifically for detecting attacker behavior.
Implementing AI Security Solutions
Start with these steps:
- Assess your needs: Determine which AI security features align with your risk profile
- Start small: Begin with one AI-powered security tool and expand gradually
- Integrate with existing systems: Ensure AI tools work alongside your current security infrastructure
- Train your team: Help staff understand how AI security systems work and how to interpret their alerts
- Monitor and adjust: Regularly review AI system performance and fine-tune settings
While AI dramatically improves security capabilities, remember that it works best when combined with human expertise. Use AI to handle the heavy lifting of threat detection and analysis, while your security team focuses on strategy and complex decision-making.
Mobile Security: Protecting Your Site on All Devices
With over 60% of web traffic now coming from mobile devices, mobile security has become a critical component of website security 2025. A mobile-optimized security strategy protects both your website and your mobile users from device-specific threats.
Mobile-Specific Security Challenges
1. Responsive Design Vulnerabilities
Mobile versions of websites sometimes implement security features differently than desktop versions, creating potential gaps. Ensure your responsive design maintains consistent security across all breakpoints.
2. App-Based Attacks
If you have a mobile app connected to your website:
- Implement certificate pinning to prevent man-in-the-middle attacks
- Use secure storage for sensitive data (never plain text)
- Regularly update mobile SDKs and libraries
- Implement jailbreak/root detection
3. Public WiFi Risks
Mobile users frequently connect through unsecured public networks. Protect them by:
- Enforcing HTTPS across all pages (not just login/checkout)
- Implementing additional encryption layers for sensitive transactions
- Using security headers to prevent mixed content
- Educating users about VPN usage on public networks
Mobile Security Best Practices for Website Security 2025
Optimize Your Mobile Security Headers
Ensure these headers are properly configured for mobile traffic:
Content-Security-Policy: Proper CSP prevents unauthorized scripts
X-Frame-Options: SAMEORIGIN prevents clickjacking
Referrer-Policy: no-referrer-when-downgrade protects user privacy
Permissions-Policy: Controls access to device features
Implement Progressive Web App (PWA) Security
If your site uses PWA technology:
- Use service workers securely (validate all requests)
- Implement proper cache management to prevent cache poisoning
- Ensure offline functionality doesn’t compromise security
- Regularly audit PWA-specific vulnerabilities
Mobile Payment Security
For e-commerce sites, mobile payment security is critical:
- Integrate trusted payment gateways (Stripe, PayPal, Square)
- Implement 3D Secure authentication
- Use tokenization to avoid storing card details
- Comply with PCI DSS standards for mobile transactions
Device Fingerprinting for Fraud Prevention
Use device fingerprinting to identify suspicious mobile activity:
- Track device characteristics without invading privacy
- Flag unusual device changes for the same account
- Detect emulators or rooted devices attempting access
- Implement risk-based authentication based on device trust scores
Testing Mobile Security
Regular mobile security testing should include:
- Mobile penetration testing: Simulate attacks specifically targeting mobile users
- API security testing: Ensure mobile app APIs are properly secured
- Network traffic analysis: Monitor mobile traffic for unusual patterns
- Cross-device testing: Verify security features work across all devices and OS versions
At YAAM Web Solutions, we specialize in mobile-first security implementations that protect your users regardless of how they access your site. Our comprehensive approach ensures your website security 2025 strategy covers every device and platform.
Zero Trust Architecture: The New Security Standard for 2025
Zero Trust Architecture has become a fundamental approach in website security 2025, operating on the principle that no user or device should be trusted by default, requiring continuous verification and strict access controls. This security model is rapidly becoming the industry standard as traditional perimeter-based security proves inadequate against modern threats.
Understanding Zero Trust Principles
Traditional security models operated on a “castle and moat” philosophy—strong perimeter defenses with implicit trust for anyone inside. Zero Trust flips this model entirely: “never trust, always verify.”
Core Zero Trust Principles:
- Verify Explicitly: Always authenticate and authorize based on all available data points
- Use Least Privilege Access: Limit user access with Just-In-Time and Just-Enough-Access (JIT/JEA)
- Assume Breach: Minimize blast radius and segment access. Verify end-to-end encryption
Implementing Zero Trust for Your Website
Step 1: Identity Verification
Every access request must be authenticated, regardless of where it originates:
- Implement multi-factor authentication for all users
- Use passwordless authentication where possible (biometrics, hardware keys)
- Verify user identity continuously, not just at login
- Monitor for unusual behavior patterns that might indicate compromised accounts
Step 2: Device Security Assessment
Before granting access, verify the security posture of the connecting device:
- Check for updated operating systems and security patches
- Verify presence of endpoint protection software
- Assess compliance with your security policies
- Block or quarantine devices that don’t meet standards
Step 3: Micro-Segmentation
Divide your network into small zones to maintain separate access:
- Segment your website admin panel from public-facing pages
- Isolate database servers with strict access controls
- Create separate environments for development, staging, and production
- Limit lateral movement capabilities if one segment is compromised
Step 4: Continuous Monitoring
Zero Trust requires constant vigilance:
- Monitor all access attempts in real-time
- Analyze user behavior for anomalies
- Log all activities for forensic analysis
- Automatically revoke access when suspicious activity is detected
Zero Trust Benefits for Website Security 2025
Implementing Zero Trust architecture provides numerous advantages:
- Reduced attack surface by eliminating implicit trust
- Better visibility into who accesses what and when
- Improved compliance with data protection regulations
- Faster detection and containment of security incidents
- Protection against insider threats
- Secure support for remote work and distributed teams
Real-World Impact: Organizations implementing Zero Trust report 70% fewer successful breaches and 60% faster incident detection compared to traditional security models.
Supply Chain Security: Protecting Your Website’s Dependencies
Threat actors are increasingly targeting vulnerabilities in supply chains, especially those with weaker security measures, to access sensitive information. Supply chain attacks have become one of the most significant website security 2025 concerns, affecting businesses of all sizes.
Understanding Supply Chain Vulnerabilities
Your website doesn’t exist in isolation. It relies on:
- Third-party plugins and extensions
- JavaScript libraries and frameworks
- Content Delivery Networks (CDNs)
- Payment processors
- API integrations
- Hosting infrastructure
- Theme developers
- Analytics platforms
Each of these represents a potential entry point for attackers. When a popular library gets compromised, thousands of websites become vulnerable simultaneously.
High-Profile Supply Chain Attacks
Recent years have seen devastating supply chain attacks:
- SolarWinds (2020): Compromised software updates affected 18,000+ organizations
- Log4j (2021): Critical vulnerability in widely-used Java library
- npm packages: Regular discoveries of malicious code in JavaScript packages
- WordPress plugins: Thousands of sites affected by compromised popular plugins
How to Secure Your Website’s Supply Chain
1. Vendor Risk Assessment
Before adding any third-party component:
- Research the developer’s security track record
- Check how actively the project is maintained
- Review security audit history
- Assess the vendor’s security practices
- Verify the legitimacy of the source
2. Dependency Management
Keep track of everything your website uses:
- Maintain an inventory of all dependencies
- Document versions and update schedules
- Use software composition analysis tools
- Monitor for known vulnerabilities
- Remove unused dependencies promptly
3. Code Verification
Verify the integrity of third-party code:
- Use Subresource Integrity (SRI) for external scripts
- Implement Content Security Policy to control what can load
- Review code changes in updates before deploying
- Use checksums to verify package authenticity
- Consider hosting critical libraries locally
4. Continuous Monitoring
With over 30,000 vulnerabilities disclosed in the past year representing a 17% increase, continuous monitoring has become essential:
- Subscribe to security advisories for your dependencies
- Use automated vulnerability scanning tools
- Monitor for unusual behavior in third-party components
- Implement runtime protection to detect anomalies
- Set up alerts for security announcements
Software Bill of Materials (SBOM)
Create and maintain a Software Bill of Materials for your website:
- List all components, libraries, and dependencies
- Document versions and sources
- Track licenses and compliance requirements
- Update regularly as components change
- Use SBOM tools to automate the process
Recommended SBOM Tools:
- Syft (open-source)
- Anchore
- OWASP Dependency-Track
- Snyk
API Security in Supply Chain
Many supply chain vulnerabilities stem from insecure APIs:
- Authenticate all API requests properly
- Encrypt API communications
- Implement rate limiting to prevent abuse
- Validate and sanitize all API inputs
- Monitor API usage for anomalies
- Use API gateways for centralized security
Website Security 2025 Reality: Supply chain attacks increased by 300% over the past two years, making this a critical area for protection efforts.
Ransomware Protection: Defending Against the Biggest Threat
Up to 20% of all breaches are ransomware attacks, with more than 150 ransomware families showing this attack vector is proliferating and increasing in sophistication. Ransomware has evolved from simple file encryption to complex double and triple extortion schemes.
Understanding Modern Ransomware Tactics
Double Extortion
Attackers now:
- Encrypt your files (traditional ransomware)
- Steal your data before encryption
- Threaten to publish stolen data if you don’t pay
This means even if you have backups, you still face data leak threats.
Triple Extortion
Some attackers go further:
- Encrypt your files
- Steal your data
- Launch DDoS attacks on your infrastructure
- Contact your customers directly with threats
Ransomware-as-a-Service (RaaS)
Ransomware using double extortion tactics has become one of the biggest cybersecurity risks businesses face in 2025. Criminal organizations now offer ransomware tools as a service, allowing even non-technical criminals to launch sophisticated attacks.
Comprehensive Ransomware Defense Strategy
Prevention Layer
The best defense is preventing ransomware from reaching your systems:
- Deploy advanced email filtering to block phishing attempts
- Use web filtering to block malicious websites
- Implement application whitelisting
- Disable macros in office documents by default
- Keep all software updated and patched
- Use endpoint detection and response (EDR) tools
Detection Layer
Catch ransomware early before it spreads:
- Monitor for unusual file activity
- Track abnormal network traffic patterns
- Use behavioral analysis to spot ransomware behavior
- Implement deception technology (honeypots)
- Set up real-time alerts for suspicious activities
Containment Layer
Limit damage if ransomware breaches your defenses:
- Segment your network to prevent lateral movement
- Implement micro-segmentation for critical assets
- Use network access control (NAC)
- Maintain offline, immutable backups
- Practice regular disaster recovery drills
Recovery Layer
Be prepared to recover quickly:
- Test backup restoration regularly (at least quarterly)
- Maintain multiple backup copies in different locations
- Keep one backup completely offline and air-gapped
- Document your recovery procedures
- Maintain relationships with incident response teams
What to Do If Ransomware Strikes
If you discover a ransomware infection:
- Immediately isolate infected systems from the network
- Don’t pay the ransom (FBI and cybersecurity experts advise against payment)
- Identify the ransomware variant using ID Ransomware or similar tools
- Check for decryptors at No More Ransom project
- Contact law enforcement and file a report
- Notify affected parties as legally required
- Restore from backups once the threat is eliminated
- Conduct post-incident review to prevent recurrence
Backup Best Practices for Ransomware Protection
Follow the 3-2-1-1-0 backup rule:
- 3 copies of your data
- 2 different media types
- 1 copy offsite
- 1 copy offline/air-gapped
- 0 errors in backup verification
Critical Backup Tips:
- Encrypt backups to protect against data theft
- Test restoration procedures monthly
- Store backups in immutable storage when possible
- Separate backup credentials from production systems
- Monitor backup success and integrity continuously
Ransomware Insurance Considerations
Cyber insurance can help mitigate financial impact:
- Covers ransom payments (though payment is discouraged)
- Provides funds for recovery efforts
- Includes legal and PR support
- Offers access to incident response teams
However, insurers are becoming more selective, requiring:
- Multi-factor authentication
- Email filtering and anti-malware
- Regular backups with offline copies
- Employee security training
- Documented incident response plans
IoT Security: Protecting Connected Devices in 2025
The proliferation of IoT devices has expanded the attack surface, with many of these devices lacking adequate security features. As businesses incorporate smart devices, cameras, sensors, and other IoT equipment, website security 2025 must extend to these endpoints.

The IoT Security Challenge
IoT devices present unique security challenges:
- Often shipped with default credentials
- Rarely receive security updates
- Limited processing power for security features
- Lack of standardized security protocols
- Difficult to monitor and manage at scale
- Often remain connected for years without maintenance
Common IoT Vulnerabilities
1. Weak Authentication
Many IoT devices use:
- Default usernames and passwords (admin/admin)
- Hard-coded credentials that can’t be changed
- No authentication requirements at all
2. Insufficient Update Mechanisms
- No automatic update capability
- Updates require manual intervention
- Vendors stop supporting older devices
- No notification system for available updates
3. Insecure Network Services
- Unnecessary open ports
- Unencrypted communications
- Vulnerable firmware
- Lack of secure boot mechanisms
4. Poor Physical Security
- Easy to access and manipulate
- USB ports and debug interfaces exposed
- No tamper detection
- Extractable storage containing credentials
Securing IoT Devices Connected to Your Website
Network Segmentation
Isolate IoT devices from critical systems:
- Create a separate VLAN for IoT devices
- Block direct communication between IoT and critical servers
- Route IoT traffic through a firewall
- Monitor all IoT network activity
Access Control
Limit who and what can interact with IoT devices:
- Change all default credentials immediately
- Use strong, unique passwords for each device
- Implement certificate-based authentication where possible
- Disable unused features and services
- Restrict physical access to devices
Monitoring and Management
Keep track of all IoT devices:
- Maintain an inventory of all connected devices
- Monitor for unusual behavior or traffic patterns
- Log all IoT device activities
- Use IoT security platforms for centralized management
- Set up alerts for unauthorized access attempts
Regular Updates
Keep IoT firmware current:
- Check for updates monthly
- Subscribe to vendor security bulletins
- Replace devices that no longer receive updates
- Test updates in non-production environment first
- Document device versions and update history
IoT Security Frameworks
Follow established IoT security frameworks:
NIST IoT Cybersecurity Framework
- Device identification
- Device configuration
- Data protection
- Logical access to interfaces
- Software/firmware updates
- Cybersecurity state awareness
IoT Security Foundation Best Practices
- Privacy by design
- Secure boot and updates
- Authorization and access control
- Cryptographic algorithms
- Security logging
Future of IoT Security in Website Security 2025
Emerging solutions include:
- AI-powered IoT monitoring: Detect anomalies in device behavior
- Blockchain for IoT: Secure device identity and communications
- 5G security features: Enhanced encryption and authentication
- Edge computing security: Process data locally with enhanced protection
- Quantum-resistant cryptography: Prepare for post-quantum threats
Cloud Security Best Practices for Website Security 2025
With remote work and cloud adoption increasing, endpoints and data flows become attractive attack targets. As more businesses migrate to cloud infrastructure, cloud security has become inseparable from overall website security 2025 strategy.
Understanding Cloud Security Challenges
Shared Responsibility Model
Cloud security is split between you and your provider:
Cloud Provider Secures:
- Physical infrastructure
- Network infrastructure
- Hypervisor
- Managed service features
You Secure:
- Data
- Applications
- Operating systems
- Network configurations
- Access management
- Client-side encryption
Many breaches occur because organizations misunderstand this division.
Common Cloud Security Misconfigurations
Catastrophic failures often stem from misconfigurations and poor alignment to security fundamentals, not sophisticated attacks:
1. Public Storage Buckets
Accidentally public Amazon S3 buckets or Azure containers expose:
- Customer databases
- Backup files
- Configuration files
- Private keys and credentials
2. Overly Permissive IAM Policies
Granting excessive permissions:
- Admin access to non-admin users
- Overly broad resource access
- Long-lived access keys
- Unused accounts with active permissions
3. Unencrypted Data
Data left unprotected:
- Data at rest without encryption
- Data in transit over unencrypted channels
- Unencrypted database backups
- Keys stored alongside encrypted data
4. Inadequate Logging
Insufficient visibility:
- Logging not enabled for critical services
- Logs not monitored or analyzed
- Log retention periods too short
- No centralized log management
Cloud Security Best Practices
Cloud Security Posture Management (CSPM)
CSPM consists of continuously monitoring cloud infrastructure to identify and remediate security risks and misconfigurations:
- Automated configuration scanning
- Compliance checking against industry standards
- Risk prioritization based on severity
- Automated remediation where possible
- Continuous compliance monitoring
Popular CSPM Tools:
- Prisma Cloud (Palo Alto Networks)
- Microsoft Defender for Cloud
- AWS Security Hub
- Google Cloud Security Command Center
- Wiz
Identity and Access Management
Implement strict IAM practices:
- Use the principle of least privilege
- Enable MFA for all cloud accounts
- Rotate access keys regularly (every 90 days)
- Use temporary credentials where possible
- Implement just-in-time access
- Audit permissions quarterly
- Remove unused accounts and roles
Data Protection
Secure data throughout its lifecycle:
- Encrypt data at rest using provider-managed or customer-managed keys
- Enforce TLS 1.3 for data in transit
- Implement data loss prevention (DLP) policies
- Classify data based on sensitivity
- Use tokenization for sensitive data
- Maintain encrypted backups in multiple regions
Network Security
Protect cloud network infrastructure:
- Use Virtual Private Clouds (VPCs) for isolation
- Implement network segmentation
- Configure security groups restrictively
- Use Web Application Firewalls (WAF)
- Enable DDoS protection services
- Monitor network traffic with flow logs
Multi-Cloud Security Challenges
Enterprises typically run workloads across AWS, Azure, GCP, and private data centers, with unique configurations complicating consistent threat visibility:
Challenges:
- Different security tools and interfaces
- Inconsistent policy enforcement
- Complex identity federation
- Varied compliance requirements
- Increased management overhead
Solutions:
- Use cloud-agnostic security platforms
- Standardize security policies across clouds
- Implement centralized identity management
- Use infrastructure-as-code for consistency
- Deploy unified security monitoring
Serverless Security
Secure serverless functions and applications:
- Limit function permissions to minimum required
- Validate all inputs rigorously
- Use environment variables for secrets (not code)
- Implement function-level authentication
- Monitor function invocations for anomalies
- Set appropriate timeout values
- Use API gateways for access control
Container Security
Protect containerized applications:
- Scan container images for vulnerabilities
- Use minimal base images
- Don’t run containers as root
- Implement network policies
- Use secrets management for credentials
- Monitor container runtime behavior
- Keep orchestration platforms updated
Regulatory Compliance and Website Security 2025
Regulations are putting increasingly stringent data handling rules with stiff penalties for violations, making proactive monitoring of cyber security trends 2025 essential to stay ahead of emerging compliance concerns. Understanding and implementing compliance requirements is crucial for website security 2025.

Major Regulatory Frameworks
GDPR (General Data Protection Regulation)
Applies to any website serving EU residents:
- Obtain explicit consent for data collection
- Provide clear privacy policies
- Allow users to access their data
- Enable data portability
- Implement right to be forgotten
- Report breaches within 72 hours
- Penalties up to €20 million or 4% of global revenue
Website Security 2025 Implementation:
- Cookie consent management
- Data encryption at rest and in transit
- Secure data deletion procedures
- Privacy by design principles
- Data protection impact assessments
CCPA/CPRA (California Consumer Privacy Act)
Protects California residents:
- Disclose data collection practices
- Allow consumers to opt-out of data sales
- Provide data access and deletion rights
- Implement reasonable security measures
- Maintain detailed data inventories
PCI DSS (Payment Card Industry Data Security Standard)
Required for handling credit card information:
- Build and maintain secure networks
- Protect cardholder data
- Implement strong access control measures
- Regularly monitor and test networks
- Maintain information security policy
Website Security Implementation:
- Use validated payment gateways
- Never store CVV codes
- Encrypt transmission of cardholder data
- Implement multi-factor authentication
- Conduct quarterly vulnerability scans
HIPAA (Health Insurance Portability and Accountability Act)
For websites handling health information:
- Ensure confidentiality of protected health information (PHI)
- Implement access controls
- Encrypt PHI in transit and at rest
- Maintain audit logs
- Conduct risk assessments
- Provide security awareness training
Compliance Management Strategies
1. Data Mapping
Understand your data landscape:
- Identify all data collection points
- Map data flows through your systems
- Classify data by sensitivity
- Document data retention periods
- Track third-party data sharing
2. Policy Development
Create comprehensive security policies:
- Privacy policy
- Data retention and deletion policy
- Incident response plan
- Access control policy
- Encryption policy
- Vendor management policy
3. Technical Controls
Implement compliance-supporting technologies:
- Data encryption tools
- Access management systems
- Logging and monitoring solutions
- Data loss prevention (DLP)
- Consent management platforms
- Automated compliance reporting
4. Regular Audits
Maintain ongoing compliance:
- Conduct internal audits quarterly
- Perform external audits annually
- Test incident response plans
- Review and update policies
- Train staff on compliance requirements
- Document all compliance activities
Emerging Regulatory Trends
Watch for new regulations affecting website security 2025:
AI Governance
New regulations around AI use:
- EU AI Act requirements
- Transparency in AI decision-making
- Bias prevention and testing
- Data rights in AI training
Data Localization
Increasing requirements for data sovereignty:
- Data must remain within specific geographic boundaries
- Local data processing requirements
- Cross-border data transfer restrictions
Breach Notification
Stricter breach disclosure requirements:
- Shorter notification timeframes
- More detailed disclosure requirements
- Direct consumer notification obligations
- Regulatory reporting expansion
Compliance Automation Tools
Streamline compliance management:
- OneTrust: Privacy and data governance platform
- TrustArc: Automated privacy compliance
- Vanta: Continuous compliance monitoring
- Drata: Automated compliance for SOC 2, ISO 27001
- Secureframe: Compliance automation platform
At YAAM Web Solutions, we help businesses navigate complex compliance requirements while implementing robust website security 2025 measures. Our compliance-focused security solutions ensure you meet regulatory obligations without compromising performance or user experience.
Frequently Asked Questions About Website Security 2025
Q1: How much does website security cost in 2025?
Basic website security 2025 can be implemented for free or at minimal cost using tools like Let’s Encrypt SSL certificates and free security plugins. Comprehensive security solutions typically range from $10-$500 monthly, depending on your website size and requirements. Professional security audits cost $500-$5,000 annually. The cost of prevention is always far less than the cost of recovery from a breach.
Q2: Can I protect my website from hackers without technical knowledge?
Absolutely! While technical expertise helps, many essential security measures are beginner-friendly. Using managed hosting with built-in security, installing security plugins with default configurations, and following basic best practices can provide substantial protection. Consider partnering with security-focused agencies like YAAM Web Solutions for comprehensive protection without requiring technical skills.
Q3: How often should I backup my website?
For active websites that change frequently, daily automated backups are recommended. For static websites or blogs with infrequent updates, weekly backups may suffice. Always perform manual backups before major updates or changes. Keep multiple backup copies: at least one local, one cloud-based, and one offsite.
Q4: What’s the most important security measure I should implement first?
If you can only implement one security measure today, make it SSL/TLS encryption (HTTPS). It protects data in transit, builds user trust, improves search rankings, and is required by modern browsers. It’s also relatively easy to implement, even for beginners.
Q5: How do I know if my website has been hacked?
Common signs include: unexpected changes to website content, unfamiliar admin accounts, significant traffic drops, slow loading times, security warnings in search results, suspicious files in your directories, unexplained outbound links, or notifications from your hosting provider. Regular monitoring and malware scanning help detect breaches early.
Q6: Do small websites really need comprehensive security?
Yes! Cybercriminals use automated tools that scan millions of websites regardless of size. Small websites are often targeted because they typically have weaker security. In fact, 43% of cyber attacks specifically target small businesses. Implementing website security best practices protects your business, customers, and reputation.
Q7: What should I do immediately after discovering a security breach?
- Don’t panic but act quickly
- Take the website offline to prevent further damage
- Change all passwords immediately
- Notify your hosting provider and security team
- Document everything for investigation
- Restore from clean backups if available
- Identify the vulnerability and patch it
- Notify affected users if data was compromised
- Report to authorities if required by law
Q8: Are WordPress websites less secure than custom-built sites?
WordPress itself is secure, but its popularity and plugin ecosystem create more potential vulnerabilities. With proper security measures—regular updates, quality plugins, strong authentication, and monitoring—WordPress can be extremely secure. Many enterprise-level organizations trust WordPress for mission-critical applications.
Q9: How effective is two-factor authentication really?
Extremely effective. Multi-factor authentication reduces breach risk by 99.9% according to industry research. Even if an attacker obtains your password through phishing or brute-force attacks, they cannot access your account without the second authentication factor. This makes two-factor authentication for admin panel one of the highest ROI security investments.
Q10: Can I rely solely on my hosting provider for security?
No. While choosing a secure hosting provider is crucial, security is a shared responsibility. Hosting providers typically handle server-level security, network protection, and infrastructure updates. You’re responsible for application-level security: keeping your CMS and plugins updated, managing user access, implementing secure coding practices, and monitoring for threats.
Q11: How does voice search impact website security in 2025?
Voice search and voice-activated assistants create new security considerations. Ensure your website’s voice-accessible features use secure authentication, encrypt all voice data transmissions, and implement proper consent mechanisms for voice interactions. As voice commerce grows, securing voice-initiated transactions becomes increasingly important.
Q12: What is the role of blockchain in website security 2025?
Blockchain technology is emerging as a security tool for website verification, distributed denial of service (DDoS) protection, and secure data storage. While still evolving, blockchain can provide tamper-proof logs, decentralized authentication systems, and enhanced data integrity verification.
Q13: How do I secure my website’s API endpoints?
API security is critical in website security 2025. Implement API keys and tokens, use OAuth 2.0 for authentication, enforce rate limiting, validate all inputs, encrypt data in transit, monitor API usage patterns, and regularly audit API permissions. Consider using API gateways that provide built-in security features.
Q14: What is the difference between vulnerability scanning and penetration testing?
Vulnerability scanning is automated and identifies known security weaknesses in your system. Penetration testing is manual, where security experts actively attempt to exploit vulnerabilities to assess real-world risk. Both are important for comprehensive website security 2025—scanning for regular monitoring, penetration testing for in-depth assessment.
Q15: How can I protect my website from ransomware attacks?
Protect against ransomware by maintaining offline, encrypted backups, keeping all software updated, implementing strong access controls, using email filtering to block malicious attachments, training employees to recognize phishing, deploying endpoint protection, and maintaining an incident response plan. Website security 2025 requires multi-layered ransomware defenses.
Conclusion: Your Next Steps in Website Security 2025
Securing your website from hackers in 2025 doesn’t require a cybersecurity degree or unlimited budget—it requires consistent application of proven website security best practices and a commitment to ongoing vigilance.
Key Takeaways
- Website security 2025 is non-negotiable for businesses of all sizes
- Implement HTTPS encryption as your foundation
- Use strong authentication with two-factor protection
- Keep everything updated—CMS, plugins, themes, and server software
- Deploy a Web Application Firewall for proactive defense
- Maintain regular, encrypted, offsite backups
- Monitor continuously and respond quickly to threats
- Follow the secure website checklist consistently
Don’t Wait Until It’s Too Late
Every day you delay implementing proper security measures is a day your website remains vulnerable to attacks. The question isn’t whether you’ll face a security threat—it’s when, and whether you’ll be prepared.
Let YAAM Web Solutions Secure Your Digital Future
At YAAM Web Solutions, we understand that website security 2025 can feel overwhelming. That’s why we offer comprehensive security solutions tailored to your specific needs and technical expertise level. Our team has protected hundreds of websites across industries, combining cutting-edge security technology with human expertise.
Our Security Services Include:
- Complete security audits and vulnerability assessments
- Professional SSL certificate installation and management
- Web Application Firewall deployment and monitoring
- Automated backup systems with encrypted cloud storage
- 24/7 security monitoring and incident response
- WordPress security hardening and maintenance
- Compliance assistance (PCI DSS, GDPR, etc.)
- Employee security training programs
Whether you need a one-time security audit or ongoing protection, we’re here to help. Visit YAAM Web Solutions to schedule your free security consultation today.
Additional Resources
Want to dive deeper into website security 2025? Check out these authoritative resources:
- NIST Cybersecurity Framework – Comprehensive security guidelines
- OWASP Top 10 – Critical web application security risks
- Cybersecurity & Infrastructure Security Agency (CISA) – Government cybersecurity resources
Remember: Security is not a destination—it’s a journey. Stay informed, stay vigilant, and stay secure. Your website, your customers, and your business depend on it.
Ready to protect your website from hackers? Contact YAAM Web Solutions today and let our experts implement a comprehensive security strategy tailored to your needs. Because when it comes to website security 2025, prevention is always better than recovery.
About YAAM Web Solutions: We’re a leading web design and development agency in Jammu and Kashmir, delivering cutting-edge digital solutions with a strong focus on security. With over 10 years of experience, we specialize in creating secure, SEO-optimized websites that drive measurable results for businesses across industries. Our ISO 27001-certified processes ensure your digital assets receive enterprise-grade protection.
Written by the YAAM Web Solutions Team – Expert web developers and cybersecurity specialists committed to helping businesses protect their digital assets. Contact us at yaamwebsolutions.com for personalized security consultations.